- What we do What we do
- How we can help How we can help
- Insights Insights
- About About
- Support Support
- Book a Demo
Kamma’s Response to CVE-2021-44228 (Apache Log4j 2 Vulnerability)
Last week a security vulnerability in the Apache Log4j 2 library was publicised. The vulnerability has been given the formal title of CVE-2021-44228, but is also being reported using the terms Log4Shell and LogJam.
This vulnerability can, under specific circumstances, allow a malicious third party to execute code on a remote server which is running an unpatched version of Log4j, potentially allowing the exploit to gain remote control of the server.
For a system to be vulnerable it requires four pieces of software infrastructure to be in place and actively used:
- The system has to be coded in Java
- The system is not using the Java Security Manager
- The Java based software system is exposed to and accepts input from the public internet
- The Java based software system uses Apache Log4j 2 to undertake logging
None of Kamma’s platform or services, in our production, integration, staging or development environments, are coded in Java and thus we would like to reassure all our customers that as a company, Kamma is unaffected by this vulnerability.
However if you would like to discuss this in greater detail or require any further information, please contact us at support@kammadata.com.

New insights: how does EPC data impact affordability assessments?
Accurate energy performance data is a must to ensure mortgage lenders can accurately assess affordability and reduce risk – here’s why.
Read more
Kamma’s Response to CVE-2024-0394 (XZ Utils Backdoor)
Last week security researchers publicised a malicious back door in the XZ Utils library, a widely used suite of software that gives developers lossless compression and is commonly used for compressing software releases and Linux kernel images. The backdoor could, under certain circumstances be used to run unauthorised code via the encrypted SSH connection protocol. […]
Read more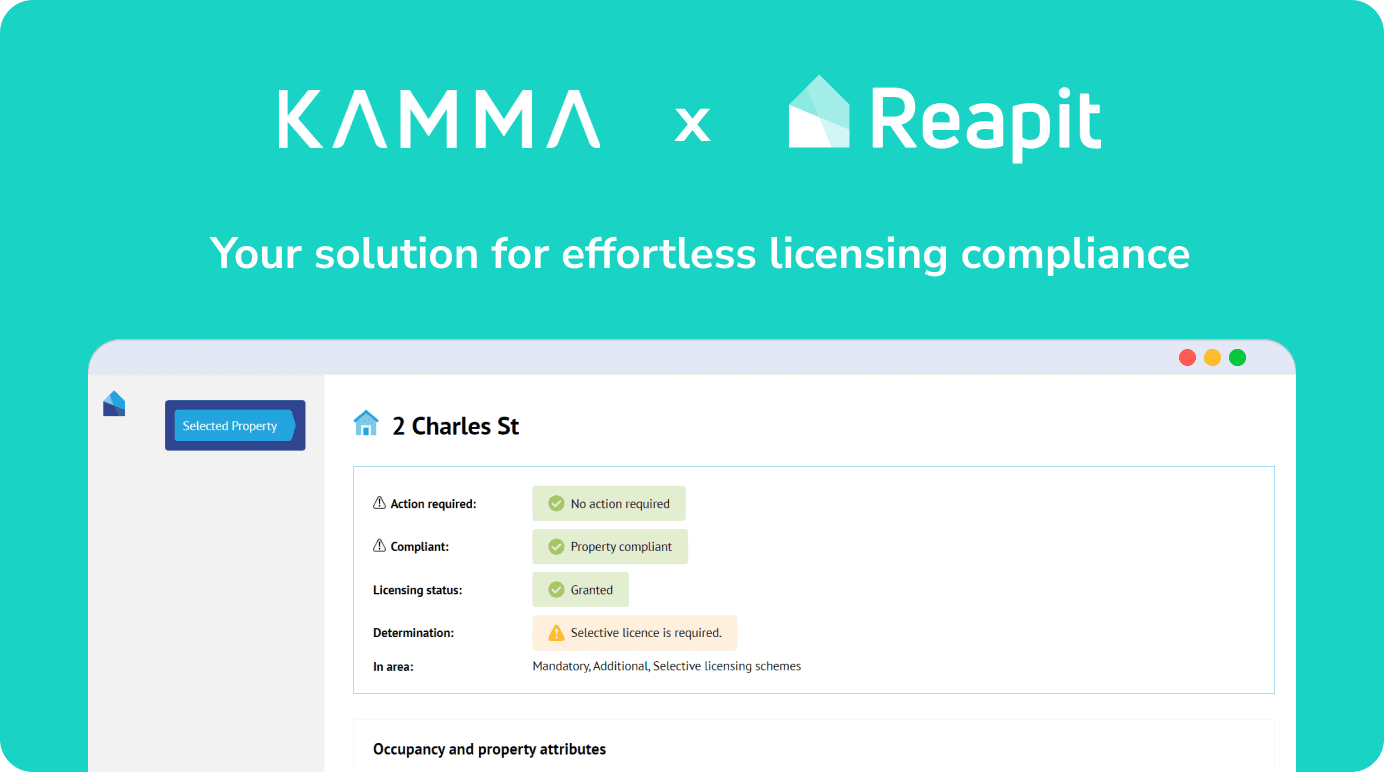
Licensing Compliance Simplified: The Kamma-Reapit Integration
The Kamma app is officially live on the Reapit marketplace! This integration arrives just in time to confront the introduction of fifteen new licensing schemes and six current consultations in the first half of the year alone. Kamma’s Reapit integration empowers you to effortlessly manage your licensing compliance through: How does the app work with […]
Read more
Subscribe to the Kamma Newsletters
Regular news, information and insights from Kamma. No spam. Unsubscribe at any time.
Subscribing ...
Sorry, we really want to but we couldn't subscribe you due to missing or incorrect information; please update the information that's highlighted in red and try again.
Well this is awkward. Something went wrong on the internet between your browser and our newletter subscription service. Please let us know and we'll do our best to fix it for you.
Thanks for subscribing! Check your Inbox in a short while for a confirmation email to check it was really you that just subscribed. If you've already subscribed, we'll keep your subscription but you won't receive a confirmation email this time.
